Written by Nerman Ahmethodžić, Software Developer

If you’ve been in software development for a while, chances are you’ve crossed paths with an old, crusty codebase—something built 10 or even 15 years ago. Maybe you had to fix a bug, add a new feature, or upgrade it to modern technologies.
These are what we call legacy applications. Well… we call them that when it’s time to upgrade. Until then, they’re just known as “production,” and everyone avoids touching them unless absolutely necessary.
But what exactly makes an app “legacy”? The term is broad, but it typically involves running on outdated frameworks and tools—think Java 8 (yes, still everywhere), older versions of Spring or Hibernate, ancient database schemas, and a whole pile of dust-covered dependencies.
So why are legacy systems such a pain to work with? A few familiar reasons:
Tangled business logic, Business rules buried in controllers, utility classes doing too much, and 300+ line methods. Code like this violates the Single Responsibility Principle and makes testing or extending the system safely a nightmare.
Outdated practices: Field injection, native SQL queries, massive application.yml files, and XML-based configurations—these patterns haven’t aged well. They once worked, but today they hurt readability, testability, and flexibility.
Virtual threads + structured concurrency is not there yet fully, structured concurrency is still in preview and might change.
Security and stability risks: Old dependencies often come with known vulnerabilities and lack modern features. Upgrading them is risky because the code isn’t modular, lacks tests, and tends to break in unpredictable ways.
No test coverage = fear of change: Most legacy code wasn’t built with testing in mind. Every fix or refactor feels like pulling the wrong Jenga block. You want to modernize—but you’re flying blind.
Tribal knowledge and missing documentation: Often, the only documentation is a 7-year-old Jira ticket. The original authors are long gone, and you’re left reverse-engineering behavior through logs and breakpoints. What might have been “best practice” years ago is now just… practice to avoid.
In this blog, I’ll share some practical tips to help bring legacy Spring Boot projects into the modern age—improving security, maintainability, and readability, while embracing a more modern development workflow.
How to untangle the mess
1. Identify the core business use cases
Start by asking questions—lots of them. Talk to product owners, business analysts, QA engineers, and anyone else who might hold pieces of the puzzle. Dig through documentation, Jira tickets, and even commit messages. Your goal in this step is to understand the business logic.
Ignore everything else for now: mapping, enrichment layers, utility methods. Just focus on the core problem the code is trying to solve.
2. Create an orchestration layer
This might sound abstract, but it really comes down to applying a fundamental principle: Single Responsibility.
Start by organizing the code into purpose-driven classes:
- Domain objects
- Validator classes
- Utility/helper classes
- …
Separate responsibilities cleanly and consistently. The goal is to create a unified, intuitive structure that makes the flow easy to follow. In many systems I’ve worked with, this architecture pattern has helped:
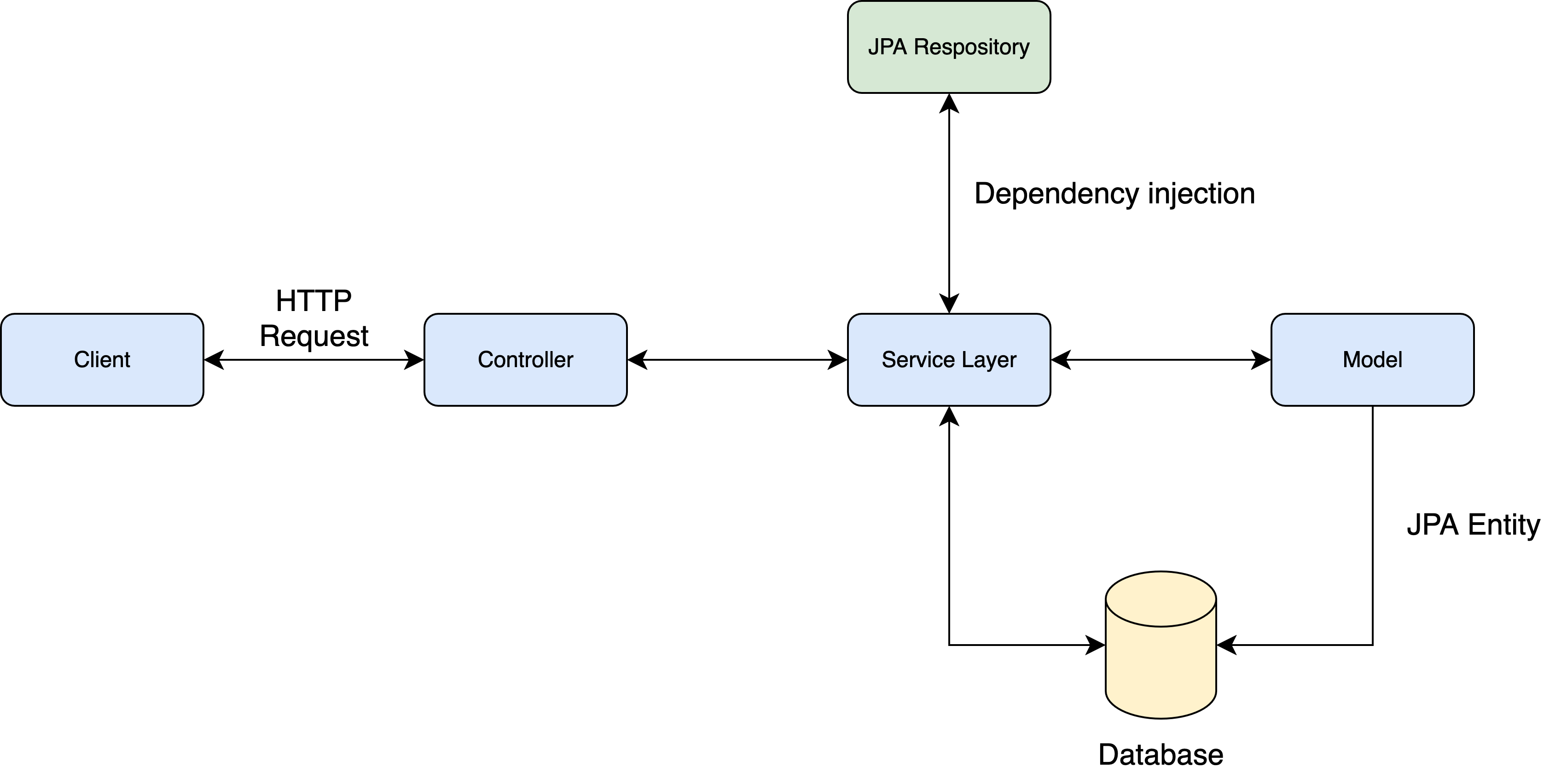
This one’s often easy to spot—those massive 300-line methods that try to do everything. Again, stick to the Single Responsibility Principle (SRP).
Forget strict rules like “no class should exceed 500 lines.” Instead, rely on intuitive signals:
- If you feel the need to add comments inside a method to explain what’s going on, that method probably needs to be split.
- If a method handles multiple concerns (e.g., validation, transformation, and persistence), it should be broken down.
Tools can help here. I highly recommend SonarLint, which detects “brain methods” (Sonar’s term) with excessive complexity. It calculates a cognitive complexity score and flags specific constructs that contribute to it, such as deeply nested if statements or excessive branching.
Field injection:
@Component
public class PaymentService {
@Autowired
private PaymentRepository paymentRepository;
public void processPayment() {
paymentRepository.save(new Payment());
}
}
Constructor injection:
@Component
public class PaymentService {
private final PaymentRepository paymentRepository;
public PaymentService(PaymentRepository paymentRepository) {
this.paymentRepository = paymentRepository;
}
public void processPayment() {
paymentRepository.save(new Payment());
}
}
4. Write Tests
Refactoring is always risky, especially in legacy codebases. Even small changes can introduce bugs in surprising places. That’s why writing tests is essential.
If there’s no existing test coverage, start by writing tests that capture the current behavior. These will act as your safety net, helping you verify that refactoring hasn’t accidentally changed functionality.
Even simple unit or integration tests can make a big difference in giving you the confidence to modernize.
Outdated practices: what to replace and why
1. Field Injection -> Constructor Injection
This one’s bothimportant and easy to fix.
Field injection hides dependencies, breaks immutability, and makes testing unnecessarily difficult. Refactoring to constructor injection makes your classes more explicit and testable—no more mysterious @Autowired fields showing up out of nowhere.
2. Massive configuration files -> Modular Configuration
One of the most common issues in legacy Spring Boot apps is having everything crammed into one huge application.yml. Database settings, credentials, feature flags, and authentication logic—it can all get mixed up and hard to manage.
Rather than just splitting by profiles, think about breaking down large configurations into smaller, more focused pieces:
- Modularize your config: Create separate config classes for different modules or features and use @ConfigurationProperties to bind properties.
- Keep it readable: Consider moving sensitive info (e.g., passwords, API keys) to external systems like environment variables or secrets managers, and reference them in the config.
By organizing the configuration this way, you make it more maintainable and reduce the risk of errors when changes are needed.
3. Native SQL in Repositories -> Spring Data JPA
To be clear: native SQL has its place. For very complex queries, it’s sometimes the only option. But as a general rule,avoid it when you can.
Why? Native queries are:
- Hard to read
- Easy to break
- Not validated at compile time
Any schema change—a renamed column, a changed type—and you’ve got a runtime error waiting to happen.
Where possible, prefer:
JPQL/HQL (e.g., @Query(“SELECT u FROM User u WHERE …”))
Criteria API (yes, it’s verbose—but type-safe)
Both options give you better integration with the JPA model and are easier to refactor safely.
4. Other honorable mentions
@Transactional in Controllers → Move to Service Layer
Controllers should handle HTTP, not database boundaries. Keep business logic (and transactions) in services.
Constants Scattered Everywhere → Centralize Them
Avoid hardcoded strings like “ACTIVE” or “US_EAST”. Use enums, config properties, or constants in dedicated classes.
Lombok Misuse
Don’t reach for @Data by default—it includes equals(), hashCode(), and toString() even when you don’t need them. Prefer @Getter/@Setter, or be explicit with what you generate.
If you’re not sure why this matters, check out this article on Lombok pitfalls (highly recommended).
These are just some of the most frequent issues I’ve seen in legacy Spring Boot projects. There are always more, but if you stick to solid principles and modern best practices, you’ll be in a much better place.
Security and stability risks – how to minimize the danger
Legacy applications often rely on outdated libraries, vulnerable dependencies, and brittle architectures. Fixing them doesn’t mean rewriting the whole app—it usually means being careful and precise about upgrades.
1. Outdated dependencies = known vulnerabilities
Using older versions of Spring, Hibernate, or Apache Commons might seem stable, but they often contain publicly known vulnerabilities—publicly being the keyword. This means attackers already know how to exploit them.
The best way to upgrade is to avoid huge version jumps. Don’t go from Spring Boot 2.4.12 straight to 3.4.5. Instead, make incremental, tested upgrades—2.4.12 → 2.6.x → 2.7.x, and so on.
Recommended tools to detect known vulnerabilities:
These tools can automatically alert you to risky dependencies and help prioritize upgrades.
2. No authentication/authorization strategy
Many legacy apps have just one role—ADMIN. You know the type.
It’s time to standardize around Spring Security, centralize your security logic in a SecurityConfig class, and introduce proper role-based access control.
Consider using:
- OAuth2 for identity provider integration (e.g., Okta, Keycloak)
- Role/permission configs stored externally (ideally in a dedicated user-management microservice)
- Avoid hardcoded roles—make your system flexible and secure
3. Lack of observability
When something goes wrong, your best (and sometimes only) friend is your logs.
Without proper logging, monitoring, and alerting, you’re flying blind. Here’s how to improve visibility:
- Logging: Use a simple but powerful tool like Logback.
- Monitoring & Alerting: Leverage Prometheus, Grafana, and Micrometer.
- Spring Boot Actuator: Expose endpoints like /health, /metrics, /env, and /loggers.
Pro tip: Build a basic dashboard that polls health and memory endpoints for all services. It can save hours of debugging by showing you early signs of trouble (e.g., high memory usage, failing health checks).
4. No test coverage
We all know the unspoken rule: “If it works, don’t touch it.”
The problem? If you don’t touch it, you can’t modernize it.
Yes, the app may have zero tests. But that’s not an excuse to avoid writing them now.
Start by capturing current behavior—not perfection, just coverage for the core logic. As mentioned earlier in the “How to Untangle the Mess” section, focus on business rules. Skip testing HTTP routing or framework glue for now.
Start with:
- Core business rule tests
- Happy-path scenarios Known edge cases
Then move on to:
- Integration tests using MockMvc or WebTestClient
- Smoke tests in CI to ensure basic uptime
Testing is a marathon. Don’t aim to write tests for every class immediately. Instead:
- Add tests when touching code (bugfixes or new features)
- Focus on critical business logic, not test coverage percentage
✅ 5 meaningful tests > ❌ 50 meaningless ones
5. Tribal knowledge and missing documentation
You’ve probably been in this situation:
You need help understanding a feature → you ask someone → they point you to someone else → eventually, you find that one person who knows everything.
If that person is on vacation, or worse—has left the company—you’re in trouble.
This is where a lack of documentation becomes a serious bottleneck. But don’t get stuck asking why the docs are missing. Focus on what you can do now:
Where to start:
- Reverse-engineer the logic
Start from known endpoints or feature triggers
Use logs and SQL tracing to identify flow and relationships
- Explore existing tests (if any)
A well-written test can be better than documentation
Use Git Blame to find who last touched relevant code
And then—document as you go:
- Add or update README.md files
- Write Javadoc or inline comments for tricky logic
- Use Confluence or internal wikis for shared knowledge
- Write tests not just for coverage, but for clarity
- Make Actuator endpoints easily visible and accessible
Think of documentation as a gift to your future self—and everyone else who will work on this app later.
Conclusion
Modernizing a legacy Spring Boot app isn’t just about upgrading dependencies or rewriting a few YAML files. It’s about peeling back years of layered decisions, tech debt, and quick fixes made under pressure.
The challenges I’ve shared—tangled business logic, outdated practices, security holes, missing tests, and vanishing documentation—are just a few of the battles I’ve personally faced. Honestly, you could write an entire book about this stuff… and people have.
If you’re dealing with legacy code, know this: you’re not alone. Most production systems are held together more by duct tape than by perfectly designed microservices. Progress usually does not come through major rewrites, but through small, safe, thoughtful changes.
Start by understanding the system. Build a safety net with tests. Refactor precisely, not recklessly.
Modernization doesn’t require perfection. It just requires consistency, care, and a willingness to leave things better than you found them.

